[Solved] The ws-management service cannot process the request. the service is configured to not accept any remote shell requests.
Infrastructure and system hardening a complex process which can take longer than expected time. Microsoft Windows provide a Microsoft security compliance kit to secure your infrastructure up to the minimal security marks which can be enhanced by adding more security using Active Directory Group Policy objects. Microsoft security compliance kid provide a predefined set of Active Directory Group Policy objects to save time for the hardening team.
CIS Bench marks are more advanced and secure set of instructions to tighten the security of Microsoft Windows Infrastructure. These Bench marks provide instructions to secure every aspect of operating systems (Windows Linux) as well as leading web servers. If you follow these CIS bench marks particularly for Windows Server 2016 or 2019 you might be blocking many items required for the administrator to perform routine jobs. Admins might be getting many issues like “The ws-management service cannot process the request. the service is configured to not accept any remote shell requests.” while installing any Microsoft Windows Server role e.g. IIS10.
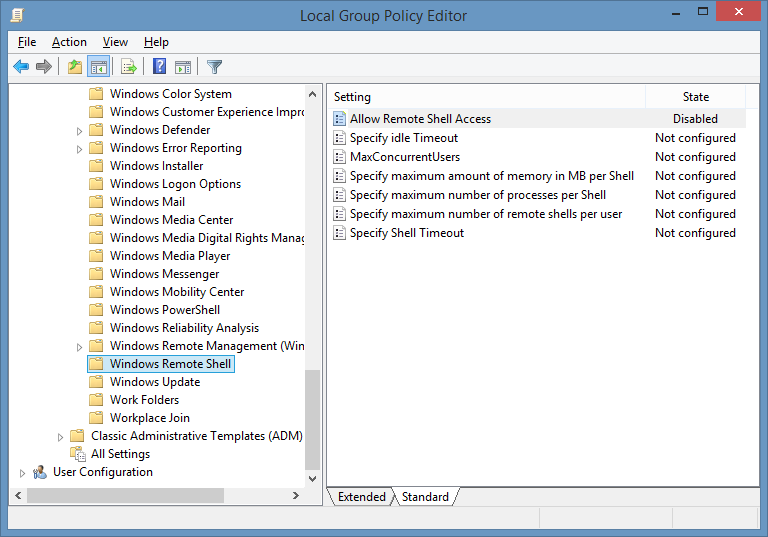
There is a group policy object which needs to be amended to resolve this issue. The setting can be located in the following group policy path to resolve the issue of “The ws-management service cannot process the request”:
Computer Configuration > Administrative Templates > Windows Components > Windows Remote Shell > Allow Remote Shell Access
Note: Once you are done with the disabling of this Group Policy Object, don’t forget to run the command gpupdate /force
As you see that this policy was recommended by CIS bench mark for extended security but some people might confused that its suggested by Microsoft which isn’t the case. This completely depend upon the security requirement from the penetration testing team that how much security settings needs to be implemented on the infrastructure to feel its secure.
However the CIS recommendation is to just disable the setting, which people mostly disagree with given the modern nature of PowerShell remoting capabilities and ease of use. Administrator must have this enabled as the primary management method but correctly configure the firewall.
Note!
Another manual solution suggested by a viewer (Apply at your own risk!)
Manually switch the registry settings (regedit.exe).
HKLM:\Software\Policies\Microsoft\Windows\WinRM\Service\WinRS\ the valor “AllowRemoteShellAccess” to (1).
Then restart the WinRM Service “Windows Remote Management (WS-Management)” and try to install IIS hopefully it will work without errors.
I’ve done all this, but still installing IIS refuses to install.
One or more predeployment tasks failed. The WS management service cannot process the request. The Service isconfigured to not accept any remote shell requests
Hi Rob,
Thanks for contacting us.
Would you be kind to confirm if you have applied the settings:
Note: Once you are done with the disabling of this Group Policy Object, don’t forget to run the command gpupdate /force
If you can share your policy settings by exporting it to me, I can check and let you know why the settings are not being applied.
Hi Same Issue.
I’ve done all this, but still installing IIS refuses to install I am having Windows Server 2016 std.
Please help!
Have you applied the correct policy and followed the article fully?
Hi
I got the same issue as @ Rob Dijkhuizen
Can I share the policy settings with u ? and how?
I got the file ready..
Check your email please
I got the same issue as Rob Dijkhuizen
Where can I send you the exported file ?
Got the same issue as Rob
How can we fix it?
Can I share the export file?
I believe there’s another setting to look at.
Computer Configuration > Administrative Templates > Windows Components > WinRm service>
Allow Remote Server Management through WinRm>
-Not configured–>This is the standard setting
-Enable
-Disable
If you disable or do not configure this policy setting the WinRm Service will not respond to requests from a remote computer regardless of whether or not any WinRm listeners are configured.
So this should be set at: ENABLE !!
Well, it still doesn’t work:
The WinRM service could not use the following listener to receive WS-Management requests. The listener is enabled but the listener does not have an IP address configured.
User Action
Check the underlying network configuration to determine if this listener has at least one valid IP. If the IP is valid, ensure that WinRM configuration does not exclude that IP address by using the following command:
winrm get winrm/config/service
Additional Data
Listener transport: HTTP
Listener address: *
output of winrm get winrm/config/service:
WSManFault
Message = The client cannot connect to the destination specified in the request. Verify that the service on the destination is running and is accepting requests.
Consult the logs and documentation for the WS-Management service running on the destination, most commonly IIS or WinRM. If the destination is the WinRM service,
run the following command on the destination to analyze and configure the WinRM service: “winrm quickconfig”.
Error number: -2144108526 0x80338012
The client cannot connect to the destination specified in the request. Verify that the service on the destination is running and is accepting requests.
Consult the logs and documentation for the WS-Management service running on the destination, most commonly IIS or WinRM. If the destination is the WinRM service,
run the following command on the destination to analyze and configure the WinRM service: “winrm quickconfig”.
output of winrm quickconfig:
WinRM service is already running on this machine.
WSManFault
Message = The client cannot connect to the destination specified in the request.
Verify that the service on the destination is running and is accepting requests.
Consult the logs and documentation for the WS-Management service running on the destination, most commonly IIS or WinRM.
If the destination is the WinRM service, run the following command on the destination to analyze and configure the WinRM service: “winrm quickconfig”.
Error number: -2144108526 0x80338012
The client cannot connect to the destination specified in the request. Verify that the service on the destination is running and is accepting requests.
Consult the logs and documentation for the WS-Management service running on the destination, most commonly IIS or WinRM.
If the destination is the WinRM service, run the following command on the destination to analyze and configure the WinRM service: “winrm quickconfig”.
I don’t know what to do next (besides installing Apache webserver instead of IIS)
I finally found the solution.
Use this command to see what ip address the WinRm service is listening to:
netsh http show iplist
in my case it was: 192.168.2.180 (the ip address of my windows server).
I added my loopback ip address 127.0.0.1
using this command: netsh http add iplisten 127.0.0.1
Now it works. I can install IIS without errors.
Thank you
Thanks it worked
Hi Rob
Tried your method – netsh http add iplisten 127.0.0.1
and it worked. Thanks for the solutions.
CHEERS! +1virtual beer.
both solutions not work for me (gpedit or netsh..)
I finally found this solution. For me the problem is that i dont know why, the changes in the gpedit policy not work fine and not change the regedit parameter correctly..
i manual switch (in regedit.exe) in the folder
HKLM:\Software\Policies\Microsoft\Windows\WinRM\Service\WinRS\ the valor “AllowRemoteShellAccess” to (1).
Then restart the WinRM Service “Windows Remote Management (WS-Management)” and I can install IIS without errors.
Miguel’s solution worked for me too. Had to manually set up the value of the policy.