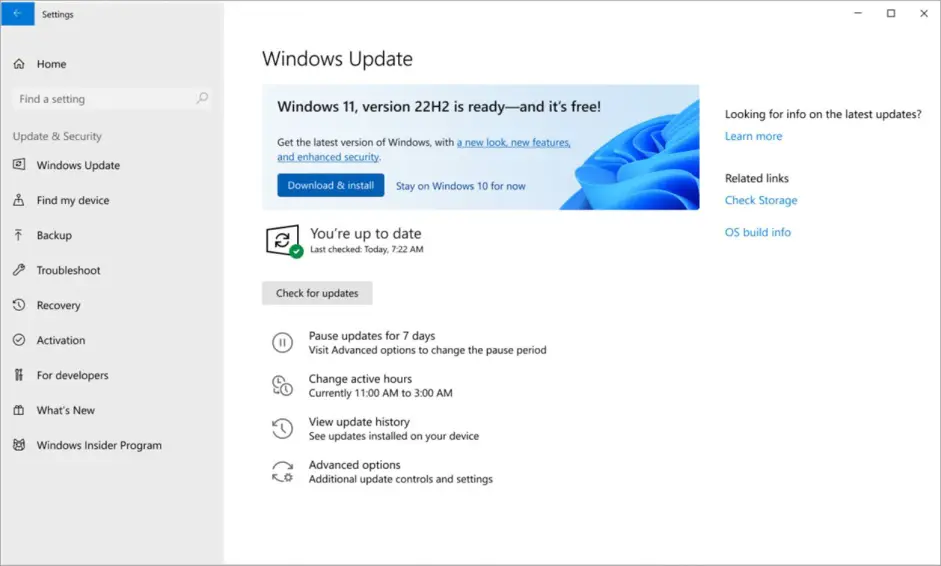
Latest windows 11 22H2 security features
Latest Windows 11 22H2 security features are added in this article. Recent revisions to Microsoft’s Windows 11 operating system have introduced a variety of additional safety measures (OS) (OS). Included on the list are better controls over apps, security against vulnerable drivers, heightened identity protection, and streamlined password management. Microsoft asserted in a blog post that its Smart App Control bundle of features provides customers with a high level of security even while making their own program choices.
IT pros believe that the operating system is substantially safer than Windows 10, especially for remote workers. Moreover, the new 22H2 upgrades extend the capabilities of 11 by giving additional capabilities in advance. Here is a brief summary of the aspects that users find most helpful. Here is all you need to know about the present state of Windows, including the most essential features of Windows 11 and forthcoming enhancements.

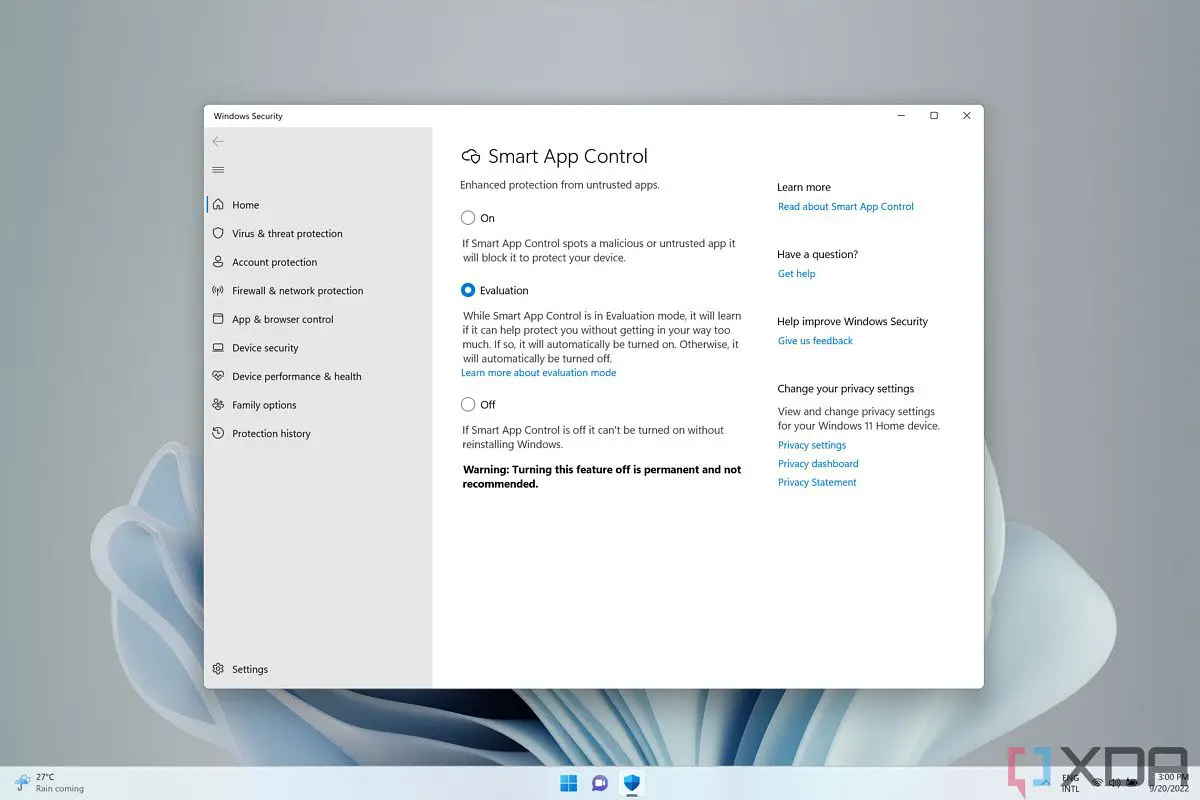
Smart App Control
It is the first time that the name Smart App Control has been used to a feature. You may recall that Windows 10 S mode only permitted the installation of programmes obtained through the Microsoft Store. Even if Smart App Control is done differently, the objective remains same.
This time, Microsoft has evaluated and recorded the hash values for a cloud-based directory of dependable software. Any installed binary will be inspected if Smart App Control is enabled on a freshly installed Windows 11 22H2. The digital signature of the request will be evaluated if it is not on the list. If the digital signature verifies as authentic, the app will be allowed to be installed. If you have a line-of-business application and wish to verify the code’s signature, contact the app’s provider. Any credible vendor practises need to follow this as a standard process.
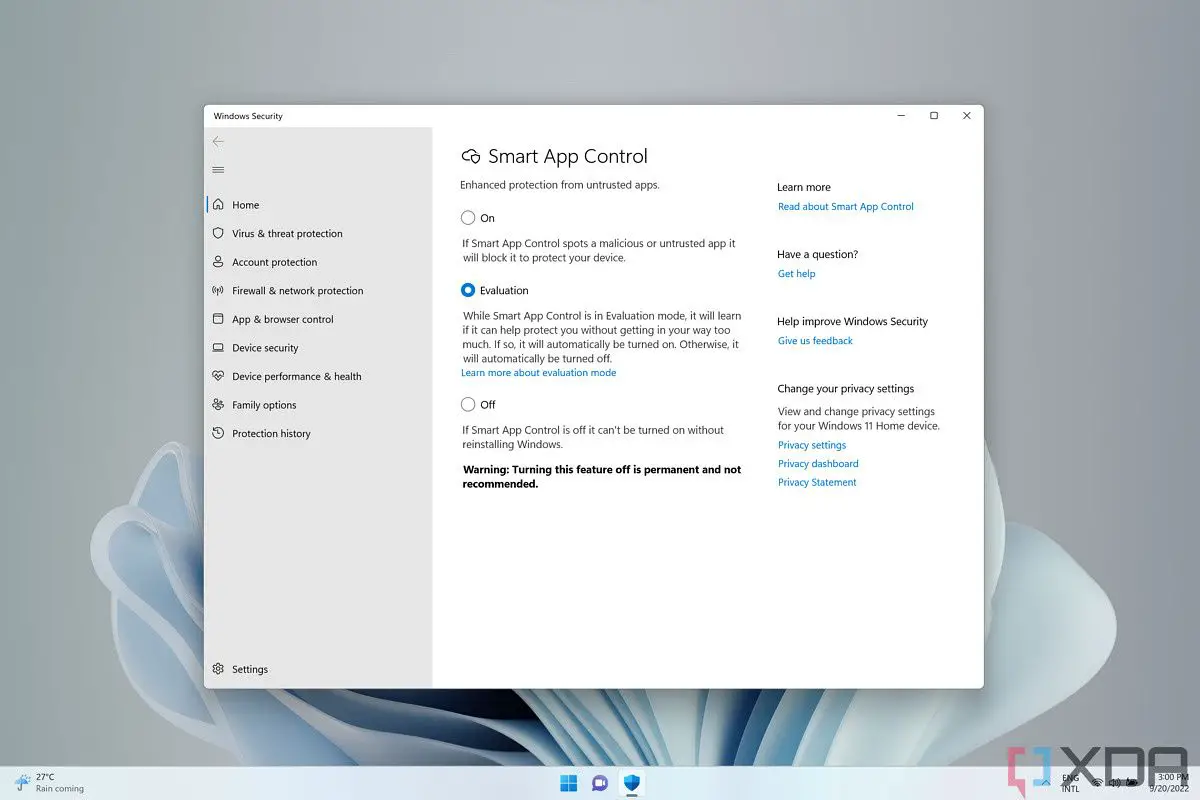
Phishing Protection
Microsoft is aggressively seeking an anti-phishing campaign while simultaneously attempting to wean customers off password-based authentication. Users are warned in 22H2 when they attempt to use their credentials on a malicious website. Windows will display a warning if a user attempts to sign in using a corporate account. Users who store passwords in WordPad or Notepad will be warned as a final precaution that is also recorded in Microsoft Defender.
Virtualization-Based Security
Microsoft is aggressively seeking an anti-phishing campaign while simultaneously attempting to wean customers off password-based authentication. Users are warned in 22H2 when they attempt to use their credentials on a malicious website. Windows will display a warning if a user attempts to sign in using a corporate account. Users who store passwords in WordPad or Notepad will be warned as a final precaution.
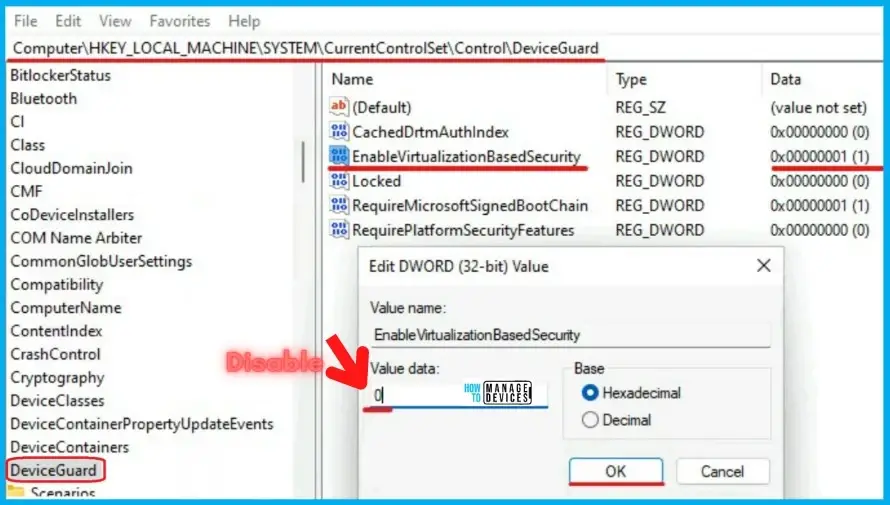
Hypervisor-Protected Code Integrity (HVCI)
Hypervisor-Protected Code Integrity (HVCI), a component of VBS, safeguards the independent memory region. By preventing the execution of Windows kernel code, hostile actors cannot hack the Microsoft kernel.
Microsoft’s 22H2 release of Kernel Mode Equipment Stack Protection will enhance the kernel code’s security, however it is hardware-dependent. Microsoft adds, “This option depends on HVCI” (Virtualization Based Protection of Code Integrity). If organisations follow the requirements, there shouldn’t be any concerns, but if they don’t, then Kernel Mode Physically Enforced Stack Protection won’t be activated.
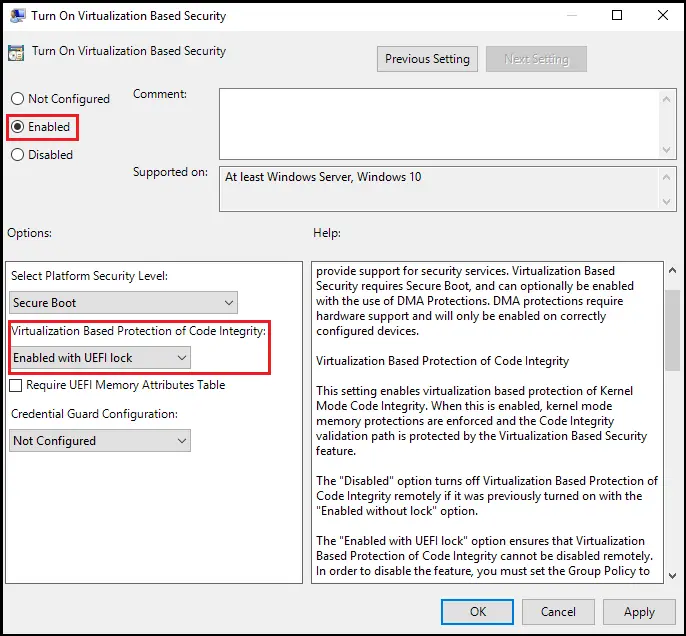
Vulnerable Driver Blocklist
Malicious drivers constitute a significant threat, but Windows 11 22H2 has taken further protections against them. Currently, Hypervisor-Protected Code Integrity (HVCI) and Windows Vulnerable Driver Block List are the two most important protections for Windows 11. Since Windows has strict requirements for code that runs in the kernel, fraudsters often exploit kernel driver vulnerabilities to get access.
Hardware-dependent Mode Kernel Hardware Imposed Stack Protection requires a CPU with Intel Tiger Lake or AMD Zen3 architectures or later. The need of an HVCI environment (Virtualization-Based Protection of Code Integrity). If your computer lacks the required hardware, you will be unable to see this page.
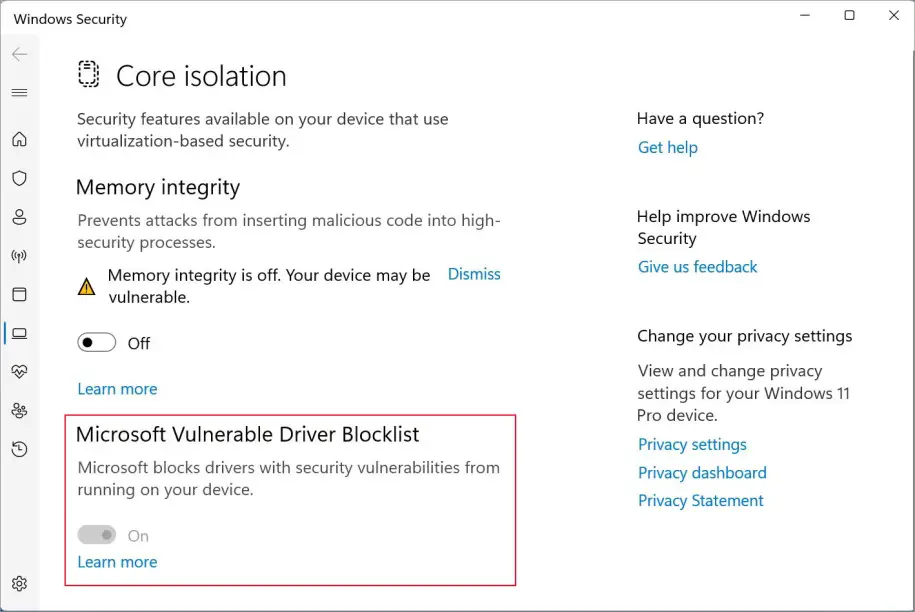
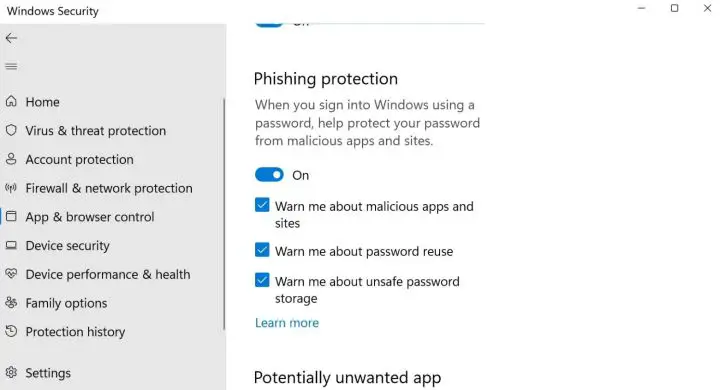
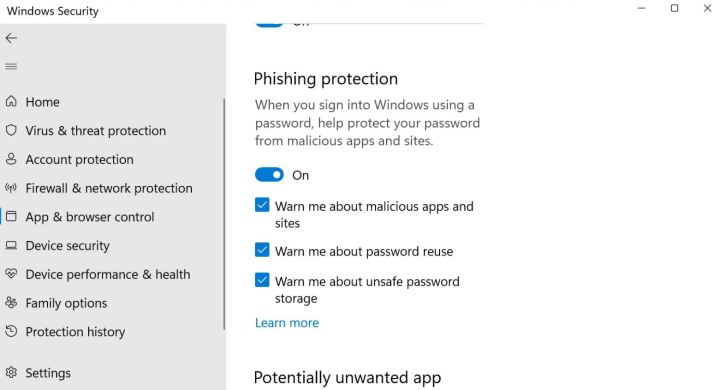
Enhanced Phishing Protection
By default, Windows 11 22H2 includes Enhanced Phishing Protection across all editions. It is not necessary to have a licence for Microsoft 365 Defender to use this feature, but doing so will grant you access to additional logging and reporting options. Users will be alerted via the Microsoft Defender SmartScreen framework whenever a website or app attempts to steal their credentials. It can also alert users if they use a corporate cert in another application or website with the proper Microsoft 365 licence. If a user saves a password in Notepad, Wordpad, or another Office application and you have licencing for Microsoft Defender for Endpoint (E5, Microsoft Business Premium, or standalone licence), this will be flagged and logged.
Printer protection
We must apply a print spooler fix to the computers in our network nearly every month. Windows 11 22H2 builds upon the previous update’s security enhancements and new printing options. In response to a Windows Print Spooler remote code execution vulnerability, the option to control the processing of queue-specific files (CopyFilesPolicy) was introduced in September 2021. (CVE-2021-36958). This setting only permits the use of the default colour profile executable (mscms.dll). Currently, both “Enabled” and “Limit queue-specific files to colour profiles” are the default safety settings for this option.
Passwordless Access
Microsoft’s authentication programme is Windows Hello. It does not need a password, and the user’s identity may be confirmed using a PIN, fingerprint, or face scan. Windows will join Apple and Google later this year in enabling passkeys, allowing users to log in without providing a password.
Zero trust
By strengthening the security of credentials, passwords, and other access restrictions, many of us are attempting to increase the efficiency with which we deploy computers. Windows 11 22H2 gives you with more options to stay one step ahead of attackers, whether you deploy with zero trust in mind or just safeguard your credentials.
After Windows 11 22H2, Microsoft will continue to seek greater network security. Despite the fact that many of us will have to wait to see them on our networks, the Windows 11 hardware requirements demonstrate the importance of security in all aspects of computing. To maintain the security of our networks, computer hardware must also play a role. Utilize these security measures by immediately testing, assessing, and implementing 22H2.
Latest windows 11 22H2 security features
Recent revisions to Microsoft’s Windows 11 operating system have introduced a variety of additional safety measures (OS) (OS). Included on the list are better controls over apps, security against vulnerable drivers, heightened identity protection, and streamlined password management. Microsoft asserted in a blog post that its Smart App Control bundle of features provides customers with a high level of security even while making their own programme choices.
IT pros believe that the operating system is substantially safer than Windows 10, especially for remote workers. Moreover, the new 22H2 upgrades extend the capabilities of 11 by giving additional capabilities in advance. Here is a brief summary of the aspects that users find most helpful. Here is all you need to know about the present state of Windows, including the most essential features of Windows 11 and forthcoming enhancements.

Smart App Control
It is the first time that the name Smart App Control has been used to a feature. You may recall that Windows 10 S mode only permitted the installation of programmes obtained through the Microsoft Store. Even if Smart App Control is done differently, the objective remains same.
This time, Microsoft has evaluated and recorded the hash values for a cloud-based directory of dependable software. Any installed binary will be inspected if Smart App Control is enabled on a freshly installed Windows 11 22H2. The digital signature of the request will be evaluated if it is not on the list. If the digital signature verifies as authentic, the app will be allowed to be installed. If you have a line-of-business application and wish to verify the code’s signature, contact the app’s provider. Any credible vendor practises need to follow this as a standard process.
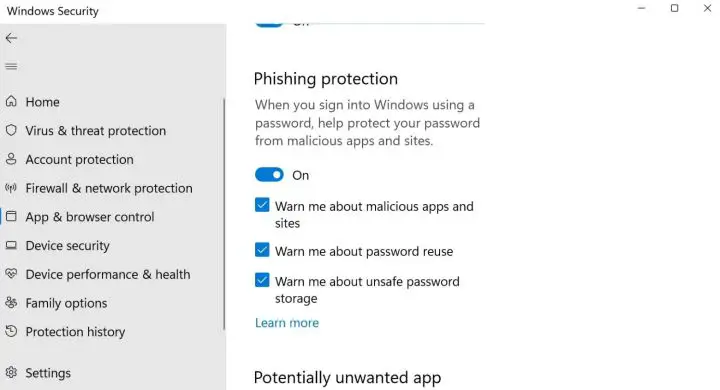
Phishing Protection
Microsoft is aggressively seeking an anti-phishing campaign while simultaneously attempting to wean customers off password-based authentication. Users are warned in 22H2 when they attempt to use their credentials on a malicious website. Windows will display a warning if a user attempts to sign in using a corporate account. Users who store passwords in WordPad or Notepad will be warned as a final precaution that is also recorded in Microsoft Defender.
Virtualization-Based Security
Microsoft is aggressively seeking an anti-phishing campaign while simultaneously attempting to wean customers off password-based authentication. Users are warned in 22H2 when they attempt to use their credentials on a malicious website. Windows will display a warning if a user attempts to sign in using a corporate account. Users who store passwords in WordPad or Notepad will be warned as a final precaution.
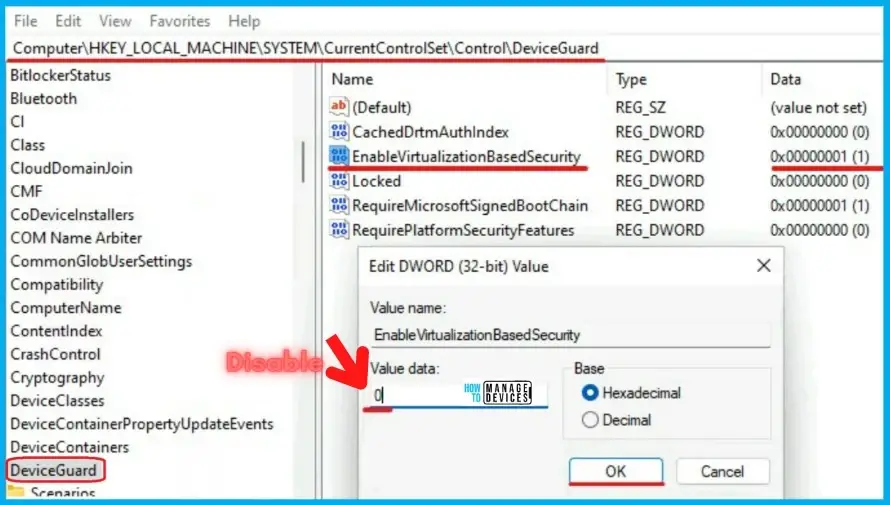
Hypervisor-Protected Code Integrity (HVCI)
Hypervisor-Protected Code Integrity (HVCI), a component of VBS, safeguards the independent memory region. By preventing the execution of Windows kernel code, hostile actors cannot hack the Microsoft kernel.
Microsoft’s 22H2 release of Kernel Mode Equipment Stack Protection will enhance the kernel code’s security, however it is hardware-dependent. Microsoft adds, “This option depends on HVCI” (Virtualization Based Protection of Code Integrity). If organisations follow the requirements, there shouldn’t be any concerns, but if they don’t, then Kernel Mode Physically Enforced Stack Protection won’t be activated.
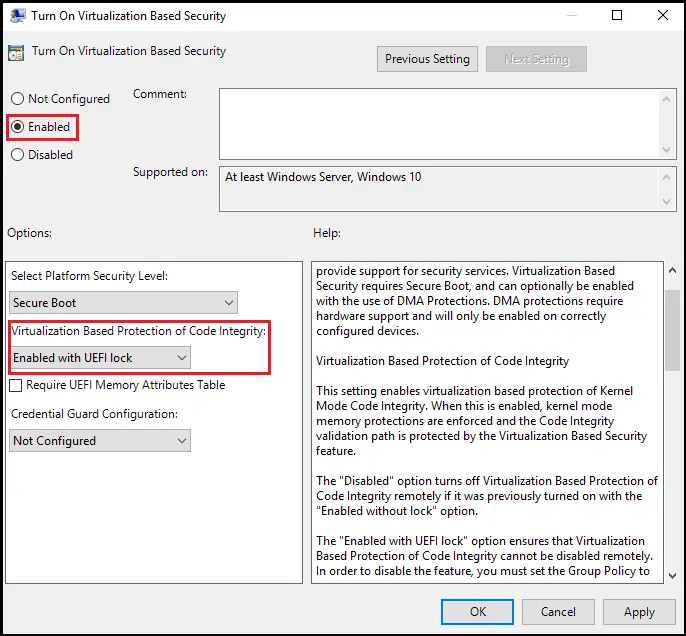
Vulnerable Driver Blocklist
Malicious drivers constitute a significant threat, but Windows 11 22H2 has taken further protections against them. Currently, Hypervisor-Protected Code Integrity (HVCI) and Windows Vulnerable Driver Block List are the two most important protections for Windows 11. Since Windows has strict requirements for code that runs in the kernel, fraudsters often exploit kernel driver vulnerabilities to get access.
Hardware-dependent Mode Kernel Hardware Imposed Stack Protection requires a CPU with Intel Tiger Lake or AMD Zen3 architectures or later. The need of an HVCI environment (Virtualization-Based Protection of Code Integrity). If your computer lacks the required hardware, you will be unable to see this page.
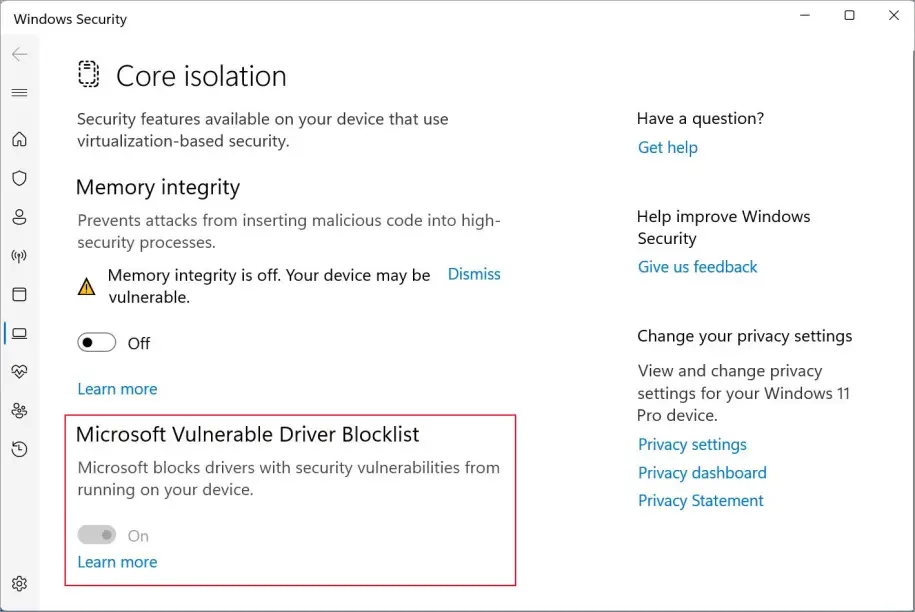
Enhanced Phishing Protection
By default, Windows 11 22H2 includes Enhanced Phishing Protection across all editions. It is not necessary to have a licence for Microsoft 365 Defender to use this feature, but doing so will grant you access to additional logging and reporting options. Users will be alerted via the Microsoft Defender SmartScreen framework whenever a website or app attempts to steal their credentials. It can also alert users if they use a corporate cert in another application or website with the proper Microsoft 365 licence. If a user saves a password in Notepad, Wordpad, or another Office application and you have licencing for Microsoft Defender for Endpoint (E5, Microsoft Business Premium, or standalone licence), this will be flagged and logged.
Printer protection
We must apply a print spooler fix to the computers in our network nearly every month. Windows 11 22H2 builds upon the previous update’s security enhancements and new printing options. In response to a Windows Print Spooler remote code execution vulnerability, the option to control the processing of queue-specific files (CopyFilesPolicy) was introduced in September 2021. (CVE-2021-36958). This setting only permits the use of the default colour profile executable (mscms.dll). Currently, both “Enabled” and “Limit queue-specific files to colour profiles” are the default safety settings for this option.
Passwordless Access
Microsoft’s authentication programme is Windows Hello. It does not need a password, and the user’s identity may be confirmed using a PIN, fingerprint, or face scan. Windows will join Apple and Google later this year in enabling passkeys, allowing users to log in without providing a password.
Zero trust
By strengthening the security of credentials, passwords, and other access restrictions, many of us are attempting to increase the efficiency with which we deploy computers. Windows 11 22H2 gives you with more options to stay one step ahead of attackers, whether you deploy with zero trust in mind or just safeguard your credentials.
After Windows 11 22H2, Microsoft will continue to seek greater network security. Despite the fact that many of us will have to wait to see them on our networks, the Windows 11 hardware requirements demonstrate the importance of security in all aspects of computing. To maintain the security of our networks, computer hardware must also play a role. Utilize these security measures by immediately testing, assessing, and implementing 22H2.