Assign Static Public IP Address to Application Load Balancer in AWS
There are multiple types of load balancers available in AWS like Azure which can be easily attached to any application for high availability and business continuity. Application and network load balancers are one of them. Mostly applications are configured behind application load balancers for security purposes. Assigning Static Public IP address to application load balancer is a tricky item. Either it requires to have a global accelerator, or you need to configure a network load balancer. In most of AWS regions it available but also not available in many regions, I was dealing with this case. If your application is configured in a region where global application accelerator is not available, you are at the right page:
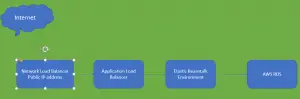
Solution!
If you have already created an application load balancer which is running successfully, you can skip step 1 otherwise follow the instructions below:
Step 1:
Create new Application Load Balancer target groups for TCP 80 and TCP 443 traffic and registering your Application Load Balancer as a target.
To create new target groups and register targets for Amazon Elastic Compute Cloud (Amazon EC2) instances, follow these steps:
1. Open the Amazon EC2 console.
2. In the navigation pane, expand Load Balancing, and then choose Target Groups.
3. Choose Create target group.
4. For Choose a target type, choose Application Load Balancer.
5. For Target group name, enter a name for the target group.
6. Select the Protocol and Port dropdown lists, and then choose protocol TCP and port 80 for HTTP traffic.
7. Select the VPC dropdown list, and then choose the VPC for your Application Load Balancer.
8. Select the Health Check protocol dropdown list, and then choose either HTTP or HTTPS for your Application Load Balancer that returns a HTTP 200-399 status.
9. Choose Next.
10. Select the Application Load balancer dropdown list, and then choose your Application Load Balancer.
11. Choose Create target group.
12. Repeat steps 3-11 to create an additional target group choosing TCP protocol and Port 443 in step 6 to create another target group for HTTPS traffic.
Step 2:
Create and configuring a Network Load Balancer to forward HTTP and HTTPS traffic to your Application Load Balancer.
To create and configure a Network Load Balancer to forward HTTP and HTTPS traffic to your Application Load Balancer, follow these steps:
1. Open the Amazon EC2 console.
2. In the navigation pane, expand Load Balancing, and then choose Load Balancers.
3. Choose Create a Load Balancer.
4. For Load balancer types, choose Network Load Balancer, and then choose Create.
5. For Load balancer name, enter a name for the Network Load Balancer.
6. In Scheme, choose either Internet-facing or Internal. An internal Application Load Balancer can be used with an internet-facing Network Load Balancer.
7. For IP address type, choose IPv4.
8. Select the VPC dropdown list, and then choose your VPC.
9. For Mappings, choose one or more Availability Zones and subnets. Choose private subnets for Internal load balancers or public subnets for internet-facing load balancers.
10. Select the IPv4 address dropdown list, and then choose either Assigned by AWS or Use an Elastic IP address.
11. Select the Protocol and Port dropdown lists, and then choose protocol TCP and port 80 for HTTP traffic.
12. Select the Default action dropdown list, and then choose the target group that contains your Application Load Balancer as registered targets.
13. Choose Add listener, and repeat steps 11-12, and then choose protocol TCP and Port 443 with a default action that forwards traffic to the TCP 443 target group for your Application Load Balancer.
14. Choose Create load balancer.
15. Follow the instructions to Test the load balancer.
Note:
- To use HTTP to HTTPS redirects on your Application Load Balancer with this configuration, you must create one Application Load Balancer target group for TCP 80 and another for TCP 443
- The security groups and NACLs attached to your Application Load Balancer must be configured to allow health checks sourced from the Network Load Balancer’s private IP address.
